PAT.Access Security

|
PAT | Access Security | Version: | 0.2 | 
|
|---|---|---|---|---|---|
| Document type: | Pattern Type | Owner: |

Description
This Pattern Type belongs to "Infrastructure Sector Business Support".
Instances of this facility are used to secure access to back-end facilities.
Protection can be needed for either (or both) of two reasons:
- to shield the protected facilities against unauthorized access;
- to shield the protected facilities from malicious or malformed traffic.
This pattern is often combined with Access Distribution; such a combination may be realized as an "access path"
Graphical Overview
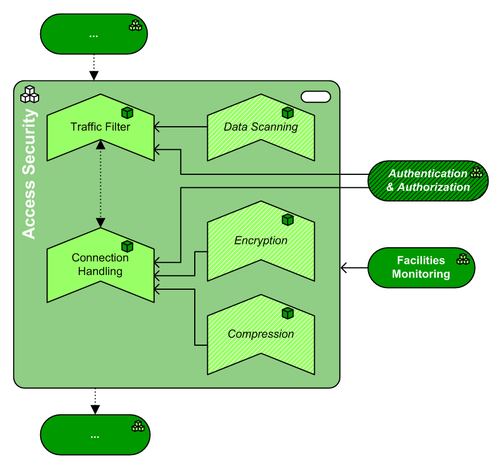
This is the graphical representation of the infrastructure functions in this Pattern Type, plus their main relations:
(The source file of this picture can be downloaded here).
Pattern Type Composition
This pattern has the following mandatory and optional subfunctions, expressed in Building Block Types:
| Icon | Function | WA | Inclusion | Rationale |
| Traffic Filtering | NW | mandatory | This facility provides the pattern with a means to reduce the attack surface of a protected facility (or a set thereof), by filtering data traffic towards and from the protected facility. Note that when filtering is not limited to traffic characteristics, then encryption and/or compression of the data transported may require the Traffic Filtering facility to use the Session Handling facility to access the data transported. | |
| Data Scanning | SE | optional | This facility provides extra capability to Traffic Filtering by scanning the data transported. Thus, Traffic Filtering can also filter traffic on data characteristics. | |
| Connection Handling | NW | mandatory | This facility terminates the user's (or client's) connection to the protected facility, and sets up its own session to that facility. This provides the Access Security pattern with the following security-related abilities:
| |
| Encryption | SS | optional | Allows encrypted communication between the end user and this pattern (necessary for private communication), even when the protected facility may not be able to do this. On the other hand, allows for decrypting encrypted traffic from the end user for inspection purposes before it enters the protected facility (or vice versa). | |
| Compression | MW | optional | Allows compressed communication between the end user and this pattern (advisable for efficient data transfer), even when the protected facility may not be able to do this. On the other hand, allows for decompressing compressed traffic from the end user for inspection purposes before it enters the protected facility (or vice versa). |
Pattern Type Neighbors
This pattern has the following mandatory and optional relations with adjacent (sub)functions, expressed in Pattern Types (PAT). Note: if the table below is empty, then there are no architecturally prescribed relations with adjacent subfunctions:
| Function | Adjacency | Description |
| Authentication & Authorization | optional | The Authentication & Authorization pattern can contain either a Permission Register, an Identity Store, or both; Access Security may use the identity store to authenticate users (usually at the location where Session Handling takes place) and/or to authorize access to the protected facilities.
Authentication can be performed at the Session Handling facility. Authorization can take place on traffic characteristics ("firewall rules") and/or on data characteristics (e.g. "access control lists") and or other conditions (e.g. the presence of up-to-date antivirus on the client's machine). |
| mandatory | Any Access Security facility must be connected to Security Management & Auditing for central management of the security measures implemented in the Access Facility itself, but also to report security incidents to a suitable central location. |
Pattern Variants based on this type
No Patterns Variants implement this Type (yet)