GP.Data Transport
| Page maturity This page has maturity level 2 (young) |
| GP | Data Transport | Version: | 0.4 | 
| |
|---|---|---|---|---|---|
| Document type: | Generic Pattern | Owner: |
| This Pattern provides the means to transport digital data between automated systems. |
Description
This Generic Pattern belongs to "Core". This Pattern provides the means to transport digital data between automated systems, within a single "Data Transport Zone", as well as to and from adjacent Data Transport Zones.
Note that the data transport over multiple Data Transport Zones with differing owners and/or security requirements must usually pass one or more Data Transport Zone Protection services, to satisfy the respecitve security requirements.
Services realized
This Pattern realizes the following service(s):
- Data Transport (This service transports data between automated systems.)
Functional and Integration view
This is the graphic representation of the functional model of this Generic Pattern:
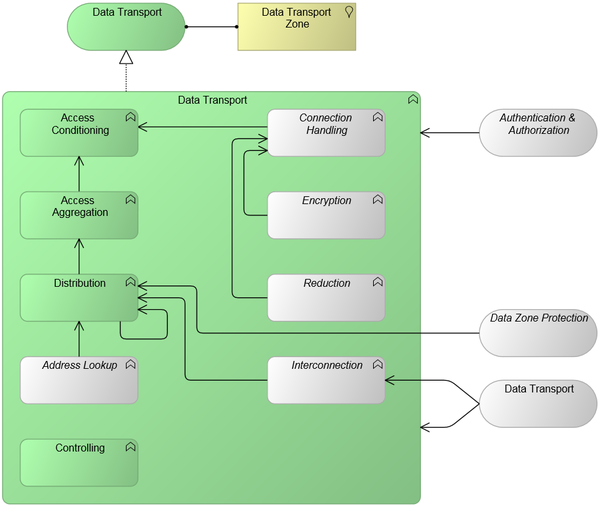
Generic Pattern Composition
This pattern is an aggregation of the following (mandatory and optional) functions, expressed in Generic Functions:
| Icon | Function | Inclusion | Rationale |
| Access Conditioning | optional | This function indicates special or additional processing that needs to occur when an infrastructure facility is going to use this Data Transport service. | |
| Distribution | recommended | This function lies at the heart of the data transport service. | |
| Name Resolution | optional | Usually an address scheme is chosen for a logical network (or combination thereof), but a different scheme of names is used by the clients (or the network internally). This facility takes care of the translation from name to address (and optionally from address to name). It is not needed in the rare case that no name schemes are in use. | |
| Interconnection | optional | When designing larger networks, then there may be a need to link multiple network segments over relatively large distances. Interconnection is the Generic Function that can provide this functionality, and it handles the challenges that are associated with networking over these longer distances. Note that this GF also allows for (unencrypted) tunneling between Data Transport Zones. | |
| Controlling | recommended | The purpose of this function within the Pattern is to focus the attention on the security aspects of an available means to read and/or alter the configuration of the Data Transport facility, thereby revealing security sensitive details and/or allow unauthorized modification of access to the Data Transport facility. | |
| Connection Handling | optional | This function supports users or systems connecting with this Data Transport Zone over a different path than a connection with this or an adjacent Data Transport Zone. The most common example of this would be a VPN connection. Note that the VPN solution itself is likely to form a Data Transport Zone separate from the Data Transport Zone that it's providing access to. | |
| Encryption | optional | It may be necessary to connect Data Transport Zones using untrusted intermediary networks (essentially all networks not under control by the organization). In this case, the tunnel between the Zones must be encrypted using this GF.
Also, the combination of Encryption and Interconnection can represent remote-connection facilities like a VPN service/dial-in service. Note however that most often it is required to route the traffic entering and leaving this remote-connection facility through the Data Zone Protection pattern. This is because users and systems connecting to the Data Transport Zone often reside in a different Data Transport Zone, security-wise. Note that when modeling a remote-connection facility, the Data Transport pattern represents a logical data transport zone that encompasses the remote users and the interlinks to the organization's remote connection facility; this zone is separate from the logical data transport zone that the users are connecting to. | |
| Reduction | optional | Just as with Encryption, it may be necessary to add extra functionality to any Interconnection. Reduction in this case can be added to make better use of the available capacity on the Interconnection. |
Services connected with this Generic Pattern
This Generic Pattern has the following mandatory and optional relations with adjacent Generic Services.
| Service | Adjacency | Summary | Rationale |
| Authentication & Authorization | optional | This service can validate an identity claim, and it can validate the permissions required for an action, as part of an Authentication & Authorization process. | If a network section needs security, this facility can be included. In essence it provides (a generic form of) access control, by performing one or more checks on the connecting infrastructure facility that tries to gain access to, or use, the network. Access controls are a form of authorization data, which are stored in an (included) Permission Register. |
| Data Zone Protection | optional | This service satisfies relevant security requirements while passing data between different Data Transport services. | Usually two logical network segments are described by different Data Transport pattern variants because the security contexts (and thus requirements) for the segments differ. If this is the case, then a connection between these segments needs to make use of this pattern Data Zone Protection, in order to ensure the right security levels in both segments. However if the network segments have the same security requirements (and differ only in characteristics and/or quality levels), then they can be linked without use of this adjacent pattern. |
| Data Transport | optional | This service transports data between automated systems. | Different Data Transport facilities can be linked - the facilities would differ in e.g. organizational ownership, security level or physical location. |
Applied Patterns based on this Generic Pattern
The following Applied Patterns are based wholly or in part on this Generic Pattern: