GP.Access Security: Difference between revisions
(intermediate save) |
(New GP complete) |
||
| Line 5: | Line 5: | ||
|version=0.3 | |version=0.3 | ||
|owner=Jan Schoonderbeek | |owner=Jan Schoonderbeek | ||
|summary=An implementation of this Pattern can be used to secure access to back-end resources. | |summary=An implementation of this Pattern can be used to secure access to back-end resources. | ||
}} | }} | ||
An implementation of this Pattern can be used to secure access to back-end resources. By and large, it performs either or both of the following two tasks: | An implementation of this Pattern can be used to secure access to back-end resources. By and large, it performs either or both of the following two tasks: | ||
| Line 20: | Line 20: | ||
{{Pattern Graphic | {{Pattern Graphic | ||
|graphic=GP.Access Security.png | |graphic=GP.Access Security.png | ||
|source=GP. | |||
|size=540px | |size=540px | ||
|title=Access Security pattern. | |||
|kind=Generic | |kind=Generic | ||
}} | }} | ||
{{Generic Pattern Composition}} | {{Generic Pattern Composition}} | ||
{{Generic Pattern Composition Row | |||
|function=GF.Filtering | |||
|choice=Must | |||
|reason=This function delivers the Pattern's core functionality, as it provides the pattern with a means to reduce the attack surface of a protected back-end resource, by filtering data traffic towards and from the protected resource. Note that when filtering is required on more than just traffic characteristics, then decryption and/or decompression of the data traffic under consideration may require the Filtering functionality to use Session Handling functionality to access the data transported. | |||
}} | |||
{{Generic Pattern Composition Row | |||
|function=GF.Data Scanning | |||
|choice=May | |||
|reason=This function provides extra capability to the Filtering function, by allowing for scanning of the data transported. This enables Filtering to filter traffic on data characteristics. | |||
}} | |||
{{Generic Pattern Composition Row | |||
|function=GF.Connection Handling | |||
|choice=Must | |||
|reason=This function terminates a consumer's connection to the protected resource, and sets up its own session to that resource. This provides the Access Security pattern with the following security-related abilities: | |||
* can access the content of encrypted sessions (e.g. SSL sessions) for inspection purposes; | |||
* can gracefully filter types of session requests/answers that are malformed or deemed inappropriate for the particular protected facility (e.g. HTTP POST). | |||
}} | |||
{{Generic Pattern Composition Row | |||
|function=GF.Encryption | |||
|choice=May | |||
|reason=Inclusion of this function allows encrypted communication between the consumer and this pattern (necessary for private communication), even when the protected back-end resource itself may not be able to do this. On the other hand, it allows for decrypting encrypted traffic from the consumer for inspection purposes, before the traffic reaches the protected resource (and vice versa). | |||
}} | |||
{{Generic Pattern Composition Row | |||
|function=GF.Reduction | |||
|choice=May | |||
|reason=Allows compressed communication between the consumer and this pattern (advisable for efficient data transfer), even when the protected resource may not be able to do this. On the other hand, allows for decompressing compressed traffic from the consumer for inspection purposes, before the traffic reaches the protected resource (and vice versa). | |||
}} | |||
{{Generic Pattern Composition Row | |||
|function=GF.Controlling | |||
|choice=Must | |||
|reason=Access to the configuration and operation of this Pattern is most always restricted. Furthermore, special care is required to ensure sufficient access to the configuration and operation whenever a security incident occurs: e.g. when a back-end resource is being attacked, Security personnel must be able to check and adapt the configuration of Access Security while the attack is underway. | |||
}} | |||
{{Table Ending}} | {{Table Ending}} | ||
{{Pattern Adjacent Services}} | {{Pattern Adjacent Services}} | ||
| Line 29: | Line 63: | ||
|service=GS.Data Transport | |service=GS.Data Transport | ||
|choice=Must | |choice=Must | ||
|reason=While virtually all Generic Patterns have a relation with Data Transport, this relation is more noteworthy for Access Security, since the designer will have to fit Access Security correctly between a Data Transport instance and the IT resource for which it is securing access. The presence of (one or more instances of) Data Transport service serves to model all concerns relating to the correct fit. | |reason=While virtually all Generic Patterns have a relation with Data Transport, this relation is more noteworthy for Access Security, since the designer will have to fit Access Security correctly between a Data Transport instance and the IT resource for which it is securing access. The presence of (one or more instances of) Data Transport service serves to model all concerns relating to the correct fit. | ||
}} | }} | ||
{{Generic Pattern Adjacent Service Row | {{Generic Pattern Adjacent Service Row | ||
| Line 47: | Line 81: | ||
|service=GS.Facilities Monitoring | |service=GS.Facilities Monitoring | ||
|choice=May | |choice=May | ||
|reason=Access Security is usually employed to secure access to the IT resource that this Pattern is protecting. Thus, many events that occur in an Access Security facility are of interest to Security staff. This means it is desirable to have the facility report directly to (a Security instance of) Facilities Monitoring. | |reason=Access Security is usually employed to secure access to the IT resource that this Pattern is protecting. Thus, many events that occur in an Access Security facility are of interest to Security staff. This means it is desirable to have the facility report directly to (a Security instance of) Facilities Monitoring. | ||
}} | }} | ||
{{Table Ending}} | {{Table Ending}} | ||
{{Text Footer GP}} | {{Text Footer GP}} | ||
Latest revision as of 17:49, 1 January 2015
| Page maturity This page has maturity level 3 (usable) |
| GP | Access Security | Version: | 0.3 | 
| |
|---|---|---|---|---|---|
| Document type: | Generic Pattern | Owner: |
| An implementation of this Pattern can be used to secure access to back-end resources. |
Description
This Generic Pattern belongs to "Business Support". An implementation of this Pattern can be used to secure access to back-end resources. By and large, it performs either or both of the following two tasks:
- It can use the combination of Connection Handling and Filter function to deny traffic to pass to the back-end resource, until proper authentication and authorization have occurred, so as to shield the protected resources against unauthorized access;
- It can use the combination of Data Scanning and a Filter function, to shield the protected resources from malicious or malformed traffic.
If needed, Encryption functionality can secure the communication between the consumers of the back-end resource and the Access Security pattern itself, and/or between the Access Security pattern and the back-end resource itself. Note that for many security operations, the traffic between consumers and back-end resources need to be unencrypted, so as to allow inspection by this Generic Pattern.
Furthermore, Reduction may be used to allow compression of the data traffic between consumers and the Access Security service, for efficient data transfers. Note that for many security operations, the traffic between consumers and back-end resources need to be uncompressed, so as to allow inspection by this Generic Pattern.
This service is often combined with Access Distribution; such a combination may be realized as an "access path".
Services realized
This Pattern realizes the following service(s):
- Access Security (This service is used to secure access to back-end resources.)
Functional and Integration view
This is the graphic representation of the functional model of this Generic Pattern:
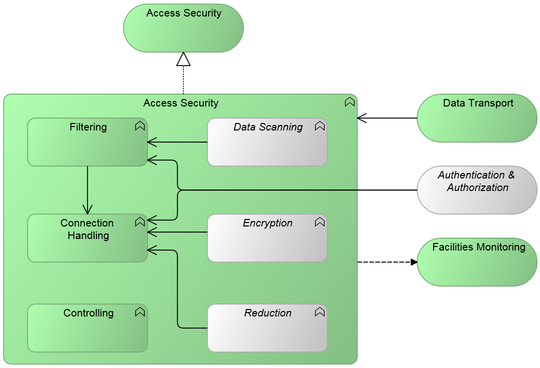
Generic Pattern Composition
This pattern is an aggregation of the following (mandatory and optional) functions, expressed in Generic Functions:
| Icon | Function | Inclusion | Rationale |
| Filtering | recommended | This function delivers the Pattern's core functionality, as it provides the pattern with a means to reduce the attack surface of a protected back-end resource, by filtering data traffic towards and from the protected resource. Note that when filtering is required on more than just traffic characteristics, then decryption and/or decompression of the data traffic under consideration may require the Filtering functionality to use Session Handling functionality to access the data transported. | |
| Data Scanning | optional | This function provides extra capability to the Filtering function, by allowing for scanning of the data transported. This enables Filtering to filter traffic on data characteristics. | |
| Connection Handling | recommended | This function terminates a consumer's connection to the protected resource, and sets up its own session to that resource. This provides the Access Security pattern with the following security-related abilities:
| |
| Encryption | optional | Inclusion of this function allows encrypted communication between the consumer and this pattern (necessary for private communication), even when the protected back-end resource itself may not be able to do this. On the other hand, it allows for decrypting encrypted traffic from the consumer for inspection purposes, before the traffic reaches the protected resource (and vice versa). | |
| Reduction | optional | Allows compressed communication between the consumer and this pattern (advisable for efficient data transfer), even when the protected resource may not be able to do this. On the other hand, allows for decompressing compressed traffic from the consumer for inspection purposes, before the traffic reaches the protected resource (and vice versa). | |
| Controlling | recommended | Access to the configuration and operation of this Pattern is most always restricted. Furthermore, special care is required to ensure sufficient access to the configuration and operation whenever a security incident occurs: e.g. when a back-end resource is being attacked, Security personnel must be able to check and adapt the configuration of Access Security while the attack is underway. |
Services connected with this Generic Pattern
This Generic Pattern has the following mandatory and optional relations with adjacent Generic Services.
| Service | Adjacency | Summary | Rationale |
| Data Transport | recommended | This service transports data between automated systems. | While virtually all Generic Patterns have a relation with Data Transport, this relation is more noteworthy for Access Security, since the designer will have to fit Access Security correctly between a Data Transport instance and the IT resource for which it is securing access. The presence of (one or more instances of) Data Transport service serves to model all concerns relating to the correct fit. |
| Authentication & Authorization | optional | This service can validate an identity claim, and it can validate the permissions required for an action, as part of an Authentication & Authorization process. | The Authentication & Authorization service can be used to authenticate consumers for the protected back-end resource (usually at the location where Session Handling takes place) and/or to authorize access to the protected back-end resource .
Authorization can also take place based on traffic characteristics, data characteristics and/or other conditions. The effect can be that consumers are denied access to the back-end resource based on many criteria, such as:
These criteria can be managed within the Access Security implementation itself, but they may just as well be managed using a separate Authorization service. |
| Facilities Monitoring | optional | This service allows its users to monitor IT facilities with the aim of guarding operational continuity or security. | Access Security is usually employed to secure access to the IT resource that this Pattern is protecting. Thus, many events that occur in an Access Security facility are of interest to Security staff. This means it is desirable to have the facility report directly to (a Security instance of) Facilities Monitoring. |
Applied Patterns based on this Generic Pattern
The following Applied Patterns are based wholly or in part on this Generic Pattern: